TLS Compliance
Topics:
Overview
Civic Platform allows agencies who are mandated with PCI security compliance to migrate to TLS 1.2. The Civic Platform server has been certified to support TLS 1.2 with inbound and outbound https communications.
The following logical diagram illustrates the inbound and outbound https Civic Platform server connections enabled with TLS 1.2:
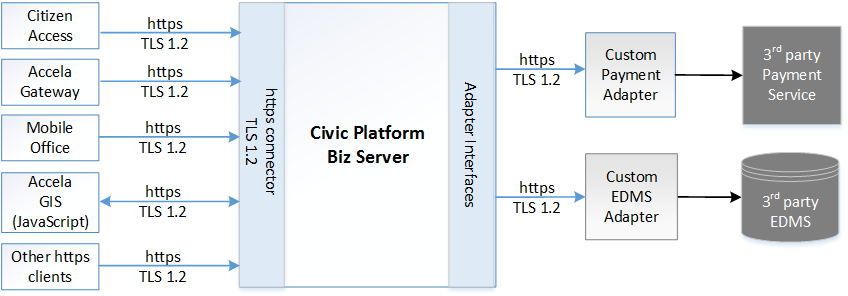
Civic Platform continues to support http connections and is backward compatible with TLS 1.0 and TLS 1.1. Although migration to TLS 1.2 is highly recommended sooner than later, self-hosted agencies can plan and implement their own timeline for migrating Civic Platform and custom adapter integrations along with their on-premise server and network environments to TLS 1.2.
Accela-hosted environments will officially migrate to TLS 1.2 at a to-be-announced date. Accela Customer Support will send out advanced notifications about the TLS 1.2 migration. During the TLS 1.2 migration, Accela will disable TLS 1.0 and 1.1 so that Civic Platform servers and applications on the Accela-hosted environments will only use TLS 1.2. To prepare for this change, Accela-hosted agencies must plan to migrate any custom integration components to TLS 1.2 and https connections to the Civic Platform server before the announced TLS 1.2 migration date.
Civic Platform components that support TLS 1.2 compliance
This section lists the integration components that have been tested with TLS 1.2 and https communications with the Civic Platform server.
Payment Adapters
Citizen Access credit card and ACH payment transactions now support TLS 1.2 using the following payment adapters:
-
CivicPay
-
PayPal Payflow Pro
-
Converge/Virtual Merchant
- Official Payments STP
-
PayPal Payflow Pro
- Converge/Virtual Merchant
- Official Payments STP
IMPORTANT:
- FirstData
- Govolution
Document Adapters
Document operations using the Accela Standard adapter, including the MTOM-enabled Standard adapter, now support TLS 1.2.
Reporting Components
- Adhoc Reports
- Crystal Reports
EMSE web service
Third-party web services invoking EMSE web services now support TLS 1.2.
Web services certified with the Civic Platform invoked by EMSE scripts also support TLS 1.2.
EMSE Tool
The EMSE Tool used for EMSE script management and deployment now supports TLS 1.2 when communicating to a third-party source code control system such as Github or SVN. This applies to both the Master script and custom script repositories.
Civic Platform components
-
Citizen Access
-
Accela GIS (JavaScript version)

The Silverlight GIS version currently does not support TLS 1.2. If your agency is using Microsoft SQL Server, refer to this Microsoft knowledge article to determine the required SQL Server patch for your SQL Server database to enable support for TLS 1.2.
-
Accela Mobile Office
- Accela Gateway (Construct API proxy)

Accela Gateway 3.2 and higher versions support TLS 1.2. Earlier Accela Gateway versions do not work if the Civic Platform biz server is enabled with TLS 1.2.
Configuration
- Enabling TLS 1.2 on the Civic Platform server
- Enabling TLS 1.2 on the Citizen Access server
- Converting certificates to Java KeyStore format
- Importing self-signed certificates
- Configuring https connections to the Civic Platform server
- Enabling TLS 1.2 on the third-party server
- Enabling TLS 1.2 on the browsers
Enabling TLS 1.2 on the Civic Platform server
Civic Platform support for TLS 1.2 requires an https listener
in the Wildfly subsystem configuration in standalone-full.xml. By
default, the Civic Platform base installer includes an https listener that is
enabled for TLS 1.2, TLS 1.1, and TLS 1.0 (for backward compatibility).
- On the av.web server, navigate to the Civic Platform installation folder, and edit the standalone-full.xml file.
- In the https listener section, change
protocol="TLSv1,TLSv1.1,TLSv1.2" to protocol="TLSv1.2":
<https-listener name="https" socket-binding="https" max-parameters="100000" security-realm="ApplicationRealm" enabled-cipher-suites="!aNULL:!ADH:!eNULL:!LOW:!EXP:!SSLv2:RC4+RSA:+HIGH:+MEDIUM:!RC4:ALL" enabled-protocols="TLSv1.2"/>
Enabling TLS 1.2 on the Citizen Access server
For TLS 1.2 support, configure the Citizen Access server to use https connections either via the Citizen Access installer or manual configuration.
- Run the Citizen Access installer, and follow the installation wizard.
- When you enter the Port number for the Civic Platform application server, change the default 3080 port number to the Civic Platform biz server’s https port number used by your agency.
- When prompted to select either the HTTP or HTTPS protocol for Citizen Access, choose HTTPS.
- On the Citizen Access server, navigate to the IIS root folder, and edit the web.config file.
- In the <webSite name="wsServer01"> element within the
<webServiceConfiguration> <webSites defaultSite="wsServer01"> section,
change the url parameter to use https and the Civic Platform biz server's https
port number used by your agency. For example:
<webServiceConfiguration> <webSites defaultSite="wsServer01"> <webSite name="wsServer01" url="https://your-agency-host.com:3443/av-aca-ws/services/" timeout="300"> <webServices> <!– This section is not shown for sample purpose only --> </webServices> </webSite> </webSites> </webServiceConfiguration>
Enabling TLS 1.2 on IIS Servers
When an agency migrates to TLS 1.2, Microsoft IIS Servers hosting client components such as Citizen Access and Accela GIS must configure the Windows server registry to only enable TLS 1.2. The security channel protocols are stored in the following registry key:
HKey_Local_Machine\System\CurrentControlSet\Control\SecurityProviders
\SCHANNEL\Protocols
In the Protocols registry key, disable the non-TLS 1.2 protocols and enable TLS 1.2. For details, see these Microsoft articles: How to disable PCT 1.0, SSL 2.0, SSL 3.0, or TLS 1.0 in Internet Information Services or Disabling TLS 1.0 on your Windows 2008 R2 server.
Note: If the IIS Server has not yet enabled https, configure the IIS Server for https. For details, see Citizen Access Administrator Guide > Implementation Planning > Enabling HTTPS.
Converting certificates to Java KeyStore format
All certificates, whether new or existing, must now be in Java KeyStore (JKS) format. This is applicable to av.biz, av.cfmx, av.indexer, and av.web servers.
To convert an existing certificate to JKS format for all necessary av.* files:
- Look up the host name in the av.{server type}/conf/av/ServerConfig.properies file
- Locate the {av.host}.crt and {av.host}.key key pair in the av.{server type}/conf/certs directory.
- Using either OpenSSL-Win64 or OpenSSL-Win32, create the necessary .p12
file by running this command:
openssl pkcs12 -export -in <av.host>.crt -passin pass:changeit -inkey <av.host>.key -out <av.host>.p12 -passout pass:changeit -name myserverkey1 - Add the new .p12 file to the Java KeyStore by running this command:
keytool -importkeystore -deststorepass changeit -destkeypass changeit -destkeystore <av.host>.jks -destkeypass changeit -srckeystore <av.host>.p12 -srcstoretype PKCS12 -srcstorepass changeit -alias myserverkey1
Importing self-signed certificates
If an integration server such as an EDMS server is using a self-signed certificate, import the self-signed certificate into the av.biz and av.web servers' certificate trusted store.
If your agency uses a self-signed certificate on the av.biz and av.web servers, import the self-signed certificate into the client component server's certificate trusted store (such as Mobile Office, Accela GIS, and Accela Gateway servers).
Configuring https connections to the Civic Platform biz server
When your agency migrates to TLS 1.2, you must update any integration component previously configured with an insecure connection (http://) to a secure protocol (https://).
Configure the following Civic Platform components connecting to the Civic Platform biz server to use secure connection URLs:
- EDMS Adapters
Go to Civic Platform Administration > Admin Tools > Standard Choices > EDMS, update the ADS_SERVER_URL to match the URL parameter of the ADS or Standard adapter to use https.
- Accela GIS (JavaScript version)
Go to JavaScript GIS Administration > {Agency} > Integrations. Update the Automation and ACA server URLs to use https, respectively.
Go to Civic Platform Administration > Admin Tools > GIS Service. Update the JavaScript API URL to use https.
- Mobile Office
When installing Mobile Office Server, on the Protocol window, you must select Enable HTTPS. (You can optionally also select the Enable HTTP option. Civic Platform currently supports both HTTP and HTTPS.)
In addition, go to Mobile Office Administration > Options > {User Group} > General Settings. Update the Application Server URL to use https for each user group.
- Accela Gateway
Go to Accela Gateway Portal > Environment Settings. In the Allowed App Servers field, update the biz server URL to use https.
Enabling TLS 1.2 on third-party components
When your agency migrates to TLS 1.2, any third-party adapter or web service that integrates with Civic Platform must enable TLS 1.2 on the third-party server. For example, if your agency uses a custom EDMS adapter, the Windows Server hosting the third-party EDMS service must enable TLS 1.2 (for details, see this Microsoft blog).
Consult the third-party vendor's documentation for details about how to enable TLS 1.2 on their server.
Enabling TLS 1.2 on the browser
When your agency migrates to TLS 1.2, client browsers connecting to Civic Platform must enable TLS 1.2. Consult the specific browser's help documentation to enable browser support for TLS 1.2.
Notes
-
TLS 1.2 support for PayPal and Converge/Virtual Merchant payment adapters was introduced in Civic
Platform versions 9.1.0, 8.0.3.0.11, 10.0.0.0.5, 7.3.3.10.4.
-
TLS 1.2 support for the EDMS standard adapter was introduced in Civic Platform version 9.1.2.